Two-factor authentication
This guide will take you through enabling two-factor authentication for your Brightbox user account.
Conventional username and password authentication is susceptible to password stealing, such as phishing attacks which trick a user into logging into a fake site and steal their credentials.
Two-factor authenticaton, also known as 2FA, protects you these kinds of issues by requiring an additional single-use code to log in, usually generated by an app on your phone.
You will need a Time-based One-Time Password (TOTP) generator such as Google Authenticator or FreeOTP.
Setup your two-factor application
Firstly, log in to Brightbox Manager as usual with your email address and password.
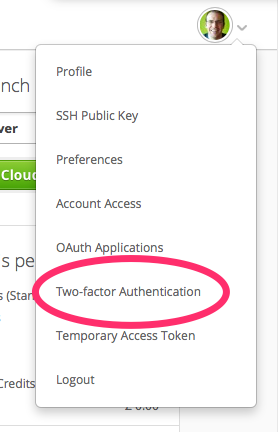
Then click the user menu up at the top right and select Two-factor
Authentication
.
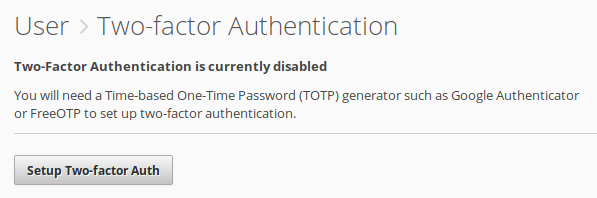
Then click the Setup Two-factor Auth
button and you’ll be presented with
a QR barcode which you should scan with your TOTP generator app.
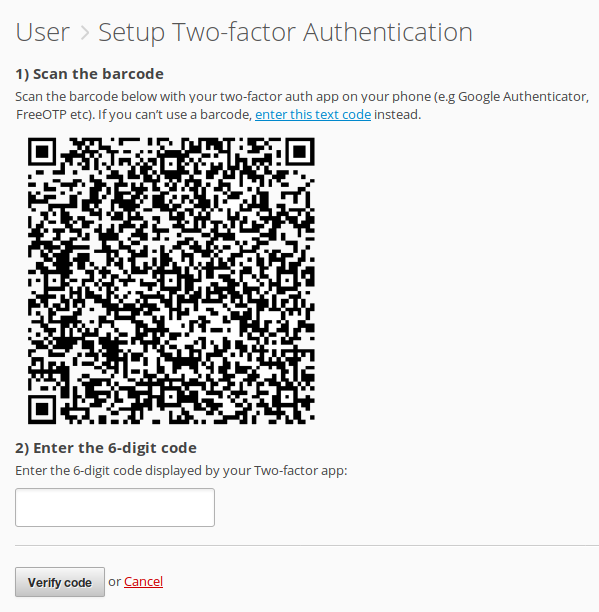
Scan the QR and a new entry should appear in your app labelled “Brightbox”. Tap
the entry to get your first code, which will be a six digit number, and enter it
into the box in Brightbox Manager and click Verify code
.
Two-factor authentication is now enabled.
Save your backup codes
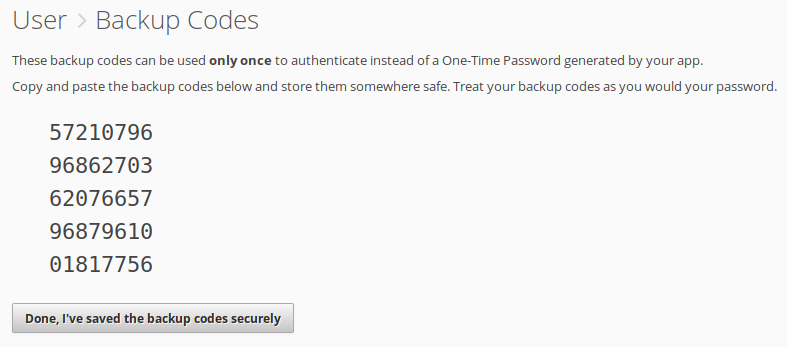
You’re now given five backup codes for use recovering access if you ever lose the ability to generate new one-time codes. Each backup code can be used only once and you cannot create any more of them, so once you’ve recovered access you should immediately reconfigure two-factor authentication with a new device.
This is the only time the backup codes are ever displayed to you, so note them down and store them securely, like you would a password.
Logging in with two-factor authentication
Different tools support two-factor authencation in different ways.
Native support
Tools that natively support two-factor will prompt you for your code explicitly.
Brightbox Manager and the Brightbox CLI natively supports two-factor authentication so after logging in as usual with your email and password you’ll then be prompted for your two-factor code before you can continue.
You’ll then only need to enter a new code if your session expires (usually a few hours) or after you explicitly log out.
Two-factor code in your password field
You can also provide your two-factor code up-front, as part of your password. This works with any existing tool that already works with Brightbox.
Enter your email address as your username as usual, then for the password enter
your password with a two-factor code tagged on the end separated by a +
character:
Email: wendy@example.com
Password: mypassword+123456
If the tool properly supports Brightbox OAuth authentication and caches the OAuth token, then you’ll only need to enter a code when your session expires (usually a couple of hours). Otherwise you’ll need to provide a new code every time you run the tool. That can be tiresome so instead you can use Temporary access tokens as your password.
Temporary access tokens
Temporary access tokens are randomly generated passwords for your user that expire after a couple of hours. You can use them in place of your password to login with any tool that doesn’t support two-factor authentication.
You can obtain a temporary access token using the Brightbox CLI:
$ brightbox token create --format=token
dd02c7c2232759874e1c205587017b9d99d9ddeeThat token can then be used with other tools as the password:
Email: wendy@example.com
Password: dd02c7c2232759874e1c205587017b9d99d9ddee